SecurEnvoy
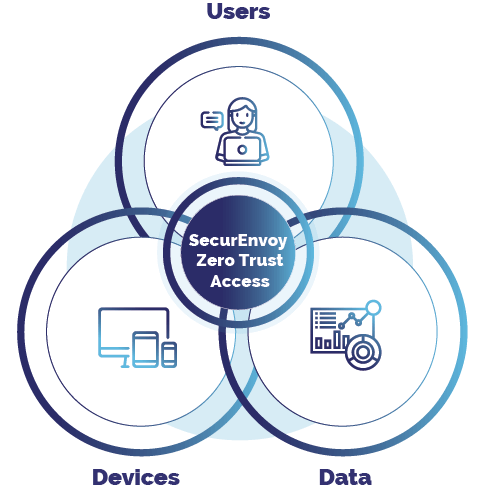
Zero trust access solution protecting your users, devices and data, wherever the location
SecurEnvoy Cybersecurity solutions engineered with zero trust in mind
SecurEnvoy provides a cyber security solution which delivers verifiable trust and data protection to organisations worldwide. The SecurEnvoy Zero Trust Access solution delivers a unique combination of trusted access management and data protection giving you the power to identify, control and protect any user, any data, on any device, wherever the location.
A true innovator, SecurEnvoy has been at the forefront of secure access management for two decades, with thousands of customers worldwide and a strong team of technical experts providing outstanding innovation and support. In 2003, SecurEnvoy brought the first-ever tokenless two-factor authentication product to market and continue to innovate and lead today with their Zero Trust Access solution comprising of advanced authentication and rapid, automated data discovery.
Bulwark Technologies is an Authorised Distributor for Securenvoy Access Management Solution and Multifactor / 2 Factor Authentication Solution
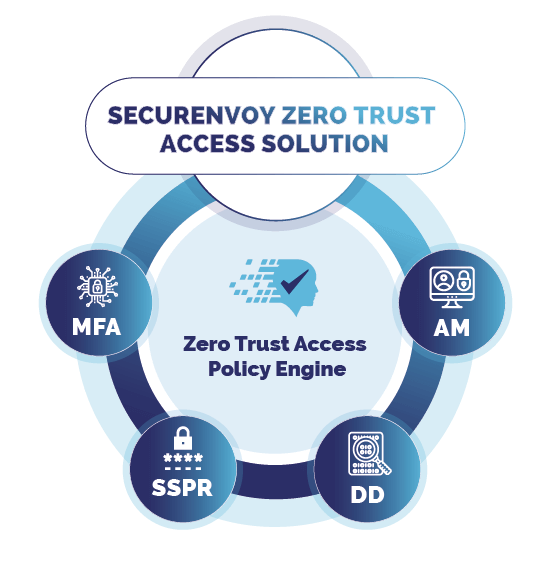
SecurEnvoy Zero Trust Access Solution
Access Management (AM)
Quick to deploy, with simple administration and an intuitive user interface, SecurEnvoy Access Management secures business assets, ensuring that only authorised users have access to the information they need, when they need it.
Multifactor Authentication
Flexible and highly customisable MFA. You decide on the platforms, devices, authentication methods and user provisioning to adapt to your needs. Serious Multi-factor Authentication from the MFA innovators.
Securenvoy Access Management (AM)
Manage access across a wide range of systems and applications, ensuring that only authorised users have access to the information they need, when they need it.
- Central to the SecurEnvoy Access Management solution is a Universal Directory, which stores and manages user identities across the entire infrastructure to provide a single reliable source of truth.
- Single Sign On (SSO) provides quick and easy user logon to all applications from anywhere and provides a centralised view to manage conditional access and dynamically onboard new applications (including legacy applications using RADIUS authentication). Users can quickly and easily update their password with Self-service Password Reset, reducing the amount of helpdesk calls.
- Conditional access to systems can be created and updated based on a user’s role, security level, the device they are using and application being accessed, along with date, time and location.
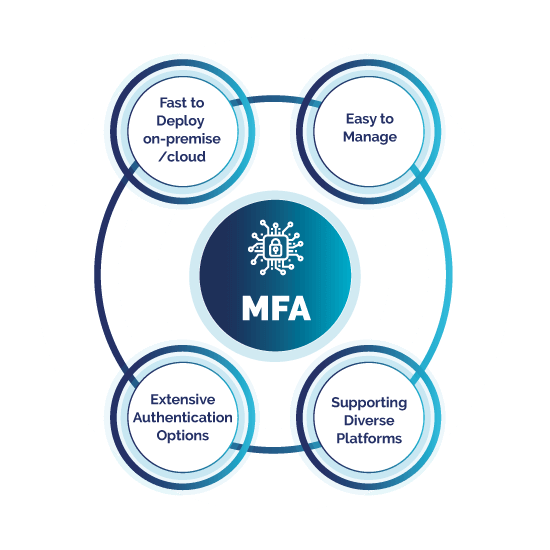
Securenvoy Multi-Factor Authentication
MFA for VPN, Remote Desktop, Web portals, Public Cloud Applications, and Server/Workstation logons.
Passwords alone are not strong enough to protect your business-critical data and assets. The elementary “username and password” approach to security is easy prey for cybercriminals. SecurEnvoy MFA provides an additional layer of security via two-factor or multi-factor authentication.
Our multi-factor authentication solution is easy to adopt and simple to use for you and your users. SecurEnvoy MFA lets you choose and set up any personal device or hardware token for authentication, making it simple for users to accept authentication requests with the device and method that suits them and your business best.
Easy for users and easy to implement on-premise and in the cloud, SecurEnvoy MFA is a cost-effective and comprehensive solution.
SecurEnvoy – Simple solutions that work
SecurEnvoy has been at the cutting-edge of innovation since 2003, originally leading the way in providing simple-to-implement Multi Factor Authentication (MFA) tools that enable organisations to be fluid but with protection.
Today they are applying those same principles through our SecurEnvoy Zero Trust Access Solution. A solution that is easy to implement, deliver extensive protection and provide an intuitive friendly end user experience. Created by the experts, fit for the challenges of today and the future.
All-round protection against breaches
Identify and ensure your data remains safe. We can help protect your business by protecting the user, the data and the device.
Optimised for speed and simplicity
Our solutions are optimised for speed and simplicity, are user-friendly, easy to manage, and easy to adopt.
Rapid deployment at scale
Designed with speed and efficiency of deployment at scale in mind. Secure the most sensitive information rapidly using our trusted technology.
