Syteca
Employee Monitoring & Insider Threat Prevention Software UEBA
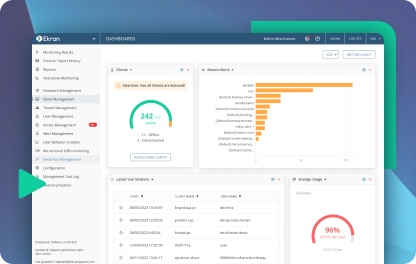
Robust and detailed employee monitoring software for insider threat detection, productivity optimization and user activity monitoring
- Monitor user activity and productivity.
- Respond to incidents.
- Manage identity and access.
Productivity Monitoring
Track and analyze the productivity of both in-house and remote employees. Detect inefficient workflows across your organization and find the true reasons behind them using data collected by Ekran System
Auto Incident Response
Receive alerts on suspicious events, such as launching an unwanted application or accessing a restricted website. Review flagged sessions to prevent inappropriate use of data inside the corporate network and eliminate security risks.
Identity & Access Management
Make sure only authorized employees can access critical endpoints. Manage access rights of privileged employees to secure access to sensitive data and get full visibility over all privileged accounts
What is Syteca
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Employee activity monitoring software that tracks any user action

Corporate servers
Secure your organization’s critical assets and prevent insider threats’ undesirable financial and reputational consequences.
Physical & virtual Desktop
Improve visibility and control over the organization’s data. Prevent and detect incidents caused by insiders in virtual and physical environments.
Remote Laptops
Monitor the activity of any user inside and outside your protected perimeter to ensure maximum security and transparency.
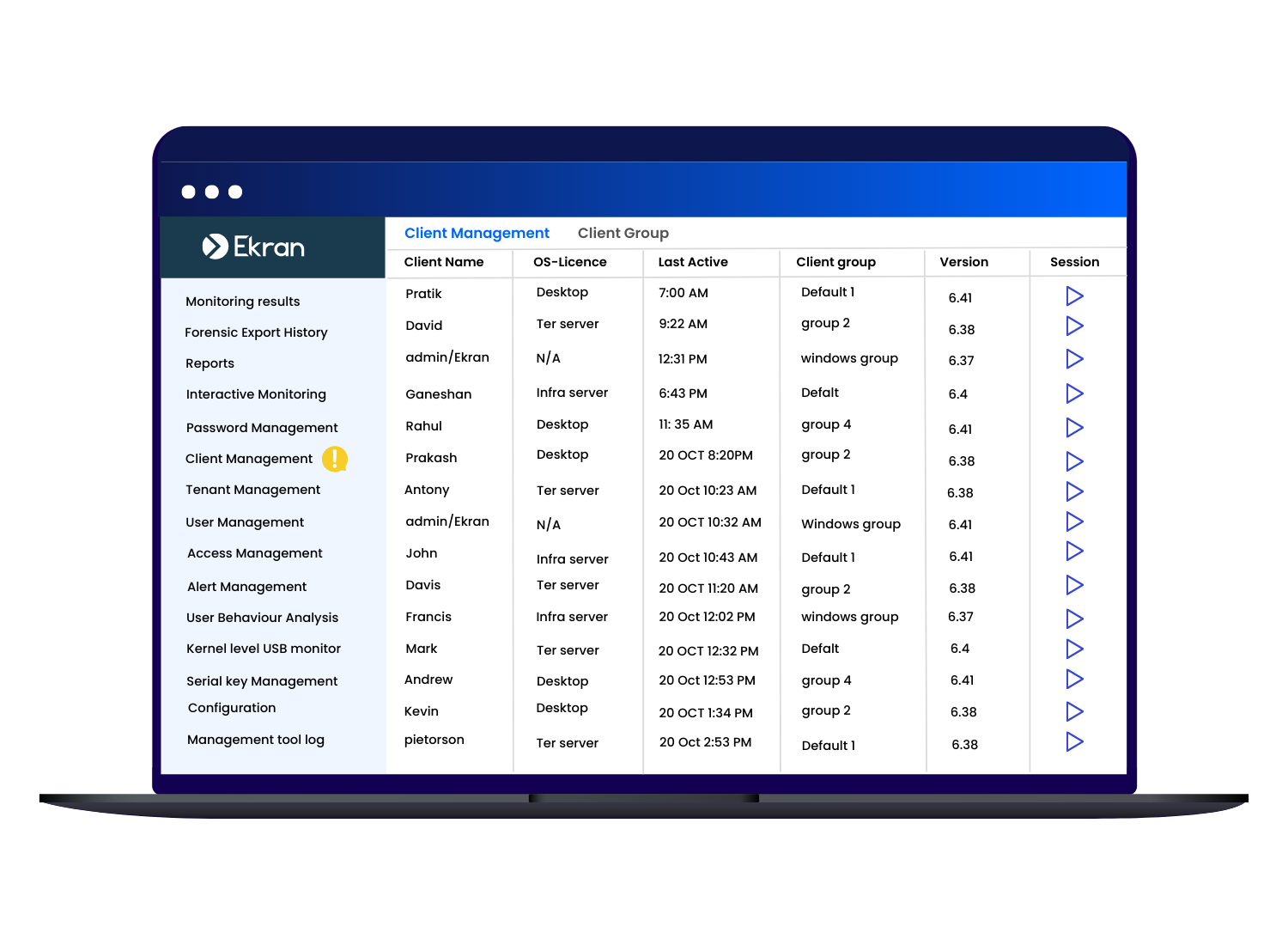
Jump Servers
Install just one Ekran System Terminal Server Client on a jump server to monitor all sessions that come through it.
Record and Monitor Everything
Productivity
Online searches
Network connections
Social media
Upload & download files
Launched Applications
Sent & received Emails
Typed Keystrokes
Visited websites
Connected USB devices
Accessed files/ systems
Screenshots
Continuous monitoring and audit functionality
Monitor employee activity in real-time and enable your security officers to watch an ongoing session without disturbing an employee. Audit employee activity and performance in real-time or in retrospective.
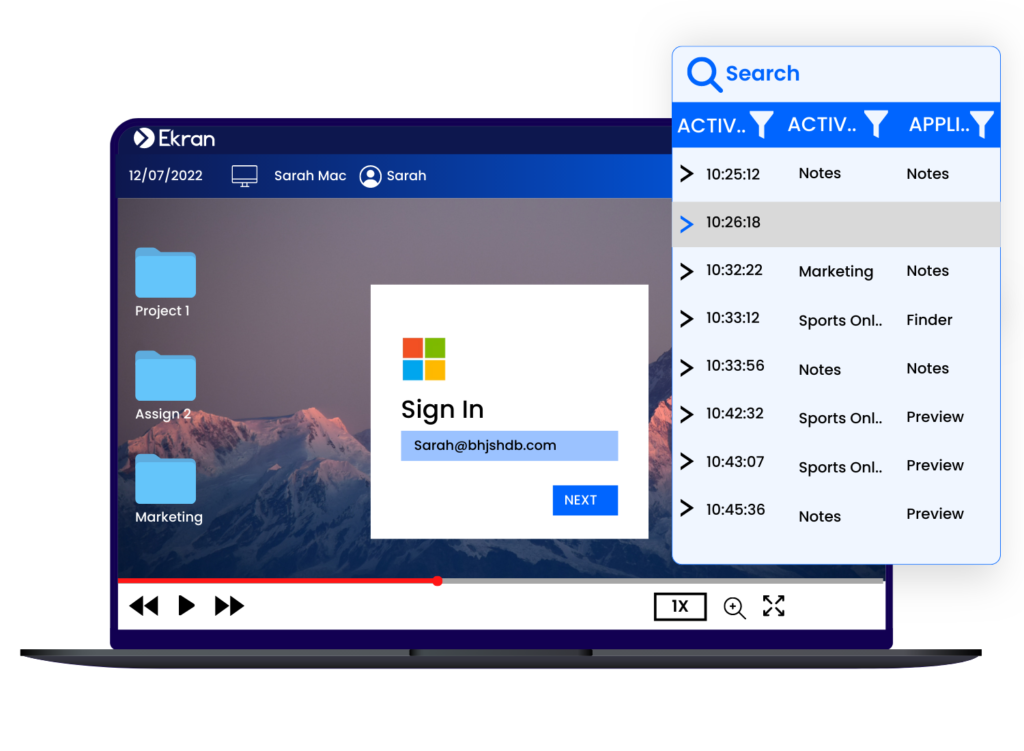
With Syteca's sessions recording software, you can streamline most cybersecurity activities in your organization as they are happening or after they've occured:
- Analyze productivity behaviours.
- Review suspicious activity
- Conduct internal and external audits
- Collect evidence for forensic activities in case of a security incident and more
All video records are indexed with multiple layers of text metadata to help you easily and quickly search for suspicious user activity. Syteca captures a large number of employee activity logs:
- The names of open applications.
- visited websites.
- executed Linux commands.
- keystrokes, and more.
Multilayer text indexing makes video records searchable by keywords and allows for in-depth investigation.
Syteca session recording works at the driver level, which makes it impossible for a user to kill the program. A built-in watchdog mechanism prevents any meddling with the recording process.
Even if an endpoint loses its internet connection, Syteca keeps recording user activity and saves data locally in a protected format. Upon the next connection, the software synchronizes data with the server.
Syteca Session Recording:
- Can't be stopped by a user
- Works in offline mode
Syteca employs a data compression algorithm to compose a lightweight recording database.
Our solution creates a master image of the user’s screen and stores user actions in the form of deltas — changes between the master image and a new screen capture. This way, recordings don’t take a lot of drive space
With a robust recording database, Syteca is perfect software for conducting swift user activity audits. Our solution also can generate a vast variety of scheduled and ad hoc reports on any event in your infrastructure.
User Activity focused Monitoring
Monitor the amount of time users have spent using a specific application within a specified time period. Also Get insights on the total time spent by the user using all applications.
Enable or disable only certain applications you want to monitor or exclude from monitoring. Eg: skip non-suspicious applications like Microsoft Word.
Record the text entered into the browser address bar at the same time record the screen capture aswell. Investigators can receive information about websites visited by users. This feature also allows you to set an alert to send notifications each time the user opens a forbidden URL.
Syteca will activate the keylogger with screen capture to also record video and audio along with metadata, regardless of the application used. Syteca is the program that records keystrokes continuously, meaning that a particular keyword can be used to initiate recording or to trigger an alert, providing a great way to limit the scope of the data you gather and let you react to incidents in a timely fashion.
continuously tracks copy, cut, and paste operations for any Windows computer and can record clipboard content, making it easy to track text data that isn’t entered directly via the keyboard.
Data recorded from the clipboard is coupled with the associated video frames, making it clear what was copied and to where, and allowing you to easily search for relevant associated events. Clipboard content can also serve as a trigger for alerts on potential incidents.

Automated Alerts and Incident Response
Respond to user activity security incidents immediately, thanks to real-time alerts
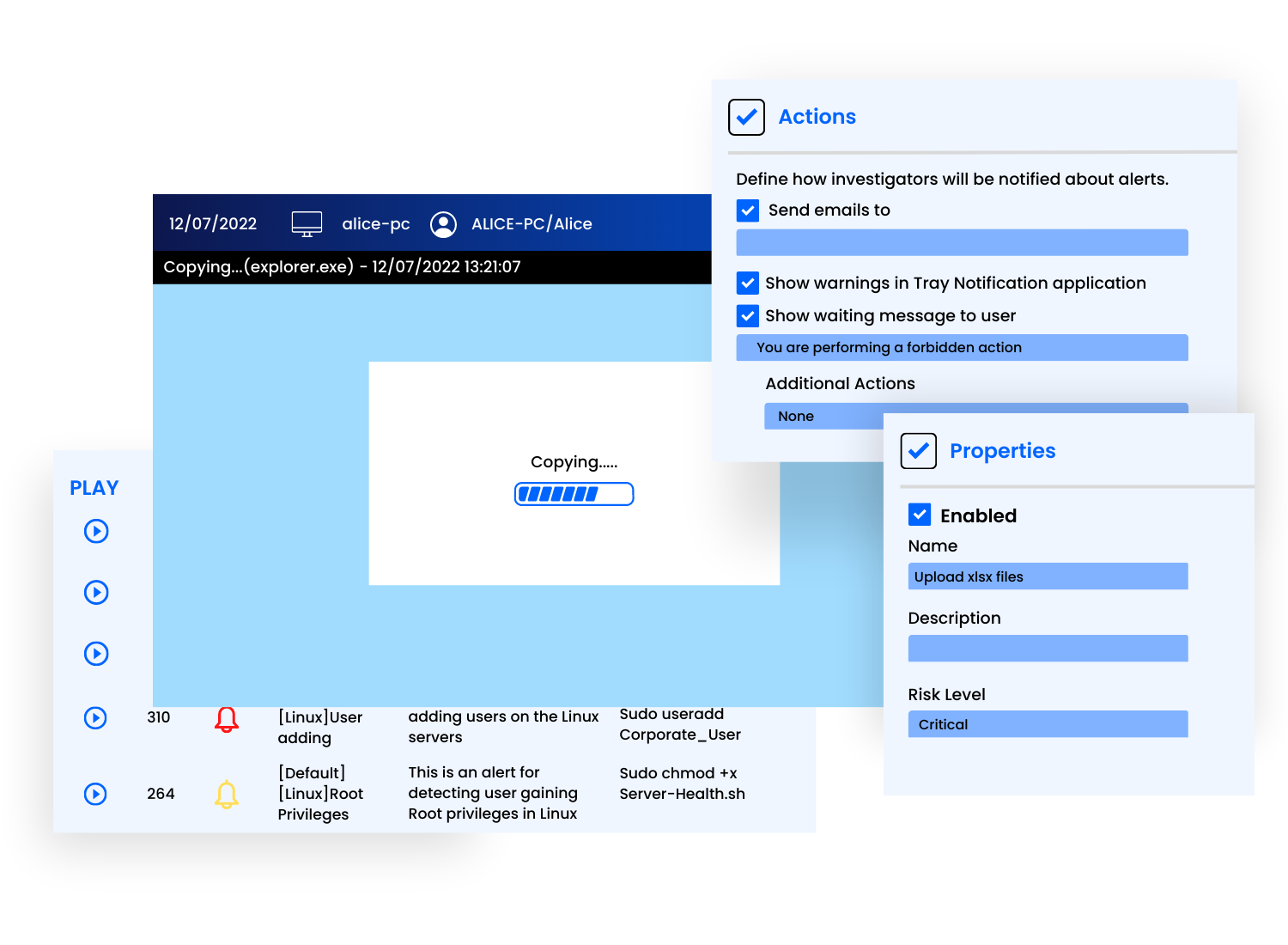
Pre-defined and Custom Alerts
Use our library of commonly used real time alerts , or build custom alerts based on certain activity parameters for any user activity security incidents. User action alerts are fully customizable. You can configure any number of rules to trigger real-time notifications and specify a risk level for each alert to prioritize alerts in monitoring records and reports.
Automated incident responds
Set up automated incident response actions for each alerts by
- Blocking the user who triggered the alert (forcing them to log out from all sessions and placing a further login restriction)
- Blocking a connected USB device of a restricted type.
- Killing the related application (process)
Identity and Access Management
Make sure only authorized employees can access critical endpoints. Manage access rights of privileged employees to secure access to sensitive data and get full visibility over all privileged accounts.
With the PAM features in Syteca, you can:
- Secure access to your Active Directory environment as well as to Linux/Unix and Windows endpoints
- Secure your web-based access
- Specify endpoints that can be accessed by particular privileged users
- Limit the time for which access is granted
- Deliver temporary credentials to specific users and groups
- Automatically generate, encrypt, and manage the credentials of privileged users
You can also use Ekran System’s PAM capabilities to ensure secure remote access to your critical endpoints for third-party vendors, contractors, and remote employees.
A sophisticated privileged password management functionality to handle and protect your secrets:
- Password Vault for securely storing and delivering secrets
- Automated and manual password rotation for Windows and AD accounts
- Role-based access control
- SSH key management
- Password management for shared accounts (Windows, Linux)
- Web account password management
FIPS 140-2 compliant encryption algorithms. All data and connections, including privileged account credentials and client–server connections, are encrypted with AES-256 keys and an RSA-1024 or RSA-2048 algorithm.
Get additional control over privileged accounts by preventing more than one user from accessing any secret at any one time, optionally limiting the time users can access secrets, and much more.
When a user logs into any particular secret, its password is checked out of the vault so that no other user can use it. When the user finishes using the secret, the password is checked back into the vault and is therefore freed up for other users.
Minimize cybersecurity risks and control the number of simultaneously active accounts with Syteca's just-in-time PAM capabilities:
- Manual access approval for determining who can access what and when
- One-time passwords (OTP) for securing temporary access to specific endpoints, including emergency access
- Integration with leading ticketing systems including SysAid and ServiceNow for cross-checking and validating the reasons for privileged access requests
- Time-based user access restrictions for enhancing the protection of critical data and systems
Monitor, record, and manage user activity in all sessions started under temporary credentials.
Strengthen the protection of your critical assets with Syteca’s two-factor authentication (2FA) tool. Runs on Windows Server and Windows and macOS endpoints. Use Our tool to protect:
- Critical endpoints, such as Windows Server (RDP)
- Privileged user logins
- Third-party logins
- Remote employee logins
Continuously monitor, record, and audit all privileged sessions on endpoints even If a server connection is temporarily limited or lost. The lightweight Syteca Client will continue recording the session in offline mode.
In addition, Syteca can automatically generate a large set of user activity reports, allowing you to get a close-up view of every user action and analyze overall user activity.
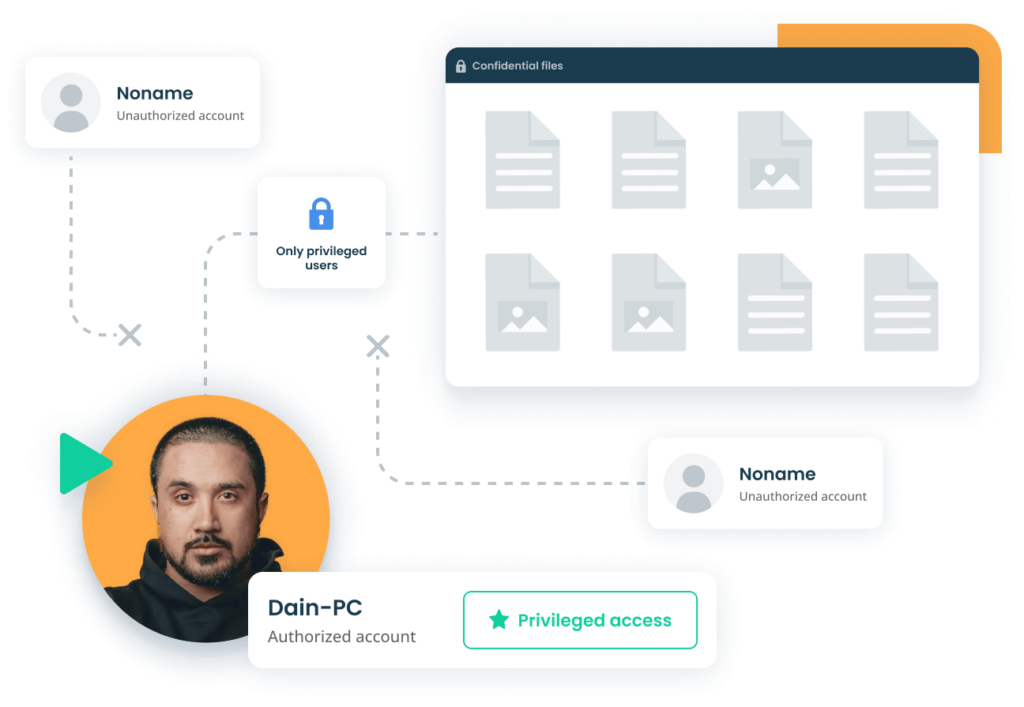
Ekran System® manages privileged access to ensure compliance




User And Entity Behavior Analytics (UEBA)
Syteca’s alert system includes an AI-based UEBA module for establishing a user behavior baseline and notifying your security team about any abnormal user activity and possible account compromise.
You can get real-time notifications via email, Detect compromised accounts, identify a malicious insider or view sessions with behavior anomalies, and quickly respond to suspicious user activity even before other security tools inform you about an incident.
Supported Platforms
Syteca’s empolyee monitoring software supports the most complete set of platforms to monitor various types of end-points and get access to all those records via a single pane of glass.








Integrate seamlessly with your stack
Syteca easily integrates with your existing infrastructure, including leading SIEM and ticketing systems.










Download Corporate Brochure
Syteca Datasheets
Product Demo
Unlock the power of Syteca tailored to your needs with Bulwark Technologies
Schedule a FREE Demo with Bulwark Technologies and explore the full potential of Syteca.
Schedule a FREE Demo
"*" indicates required fields