Heimdal Security EDR
Endpoint Detection and Response EDR Software from Heimdal Security
Heimdal’s Endpoint Detection and Response Unique prevention, threat-hunting, and remediation capabilities, empowering you to quickly and effortlessly respond to sophisticated malware.
HEIMDAL® Security EDR - Endpoint Detection and Response Software
Heimdal® Endpoint Detection and Response provides unique prevention, threat-hunting, and remediation capabilities, empowering you to quickly and effortlessly respond to sophisticated malware. Heimdal Endpoint Detection and Response grants you access to all the essential cybersecurity layers your business needs to protect itself against both known and unknown online and insider threats.
Bulwark Technologies is an authorized value-added distributor for Heimdal Security (EDR) Endpoint Detection and Response solution
What's included in our EDR Solution
One Agent - Six Solutions
Individually as products or together as a suite, Bulwark Technologies along with Heimdal® gives you unmatched flexibility in tailoring your cybersecurity defenses and scaling up any existing setup. Our EDR solution combines the most advanced threat-hunting technologies in existence:
DNS Security
Secure your hybrid workforce, either on-site or remote, with a trailblazing DNS security solution
Vulnerability Management
Deploy and Update any Microsoft, 3rd party software from anywhere in the world and according to schedule
Next Gen Antivirus with MDM
Detect online threats like ransomware, hidden backdoors, rootkits, brute-force attacks and un-detectable malware
Ransomware Protection
100% signature-free solution. Protection against malicious encryption attempts initiated during ransomware attacks.
Privilege Access Management
Manage user permissions with automatic de-escalation of user rights on threat detection. Improve Endpoint Security
Application Control
Application management solution for whitelisting and blocking of executing malicious applications.
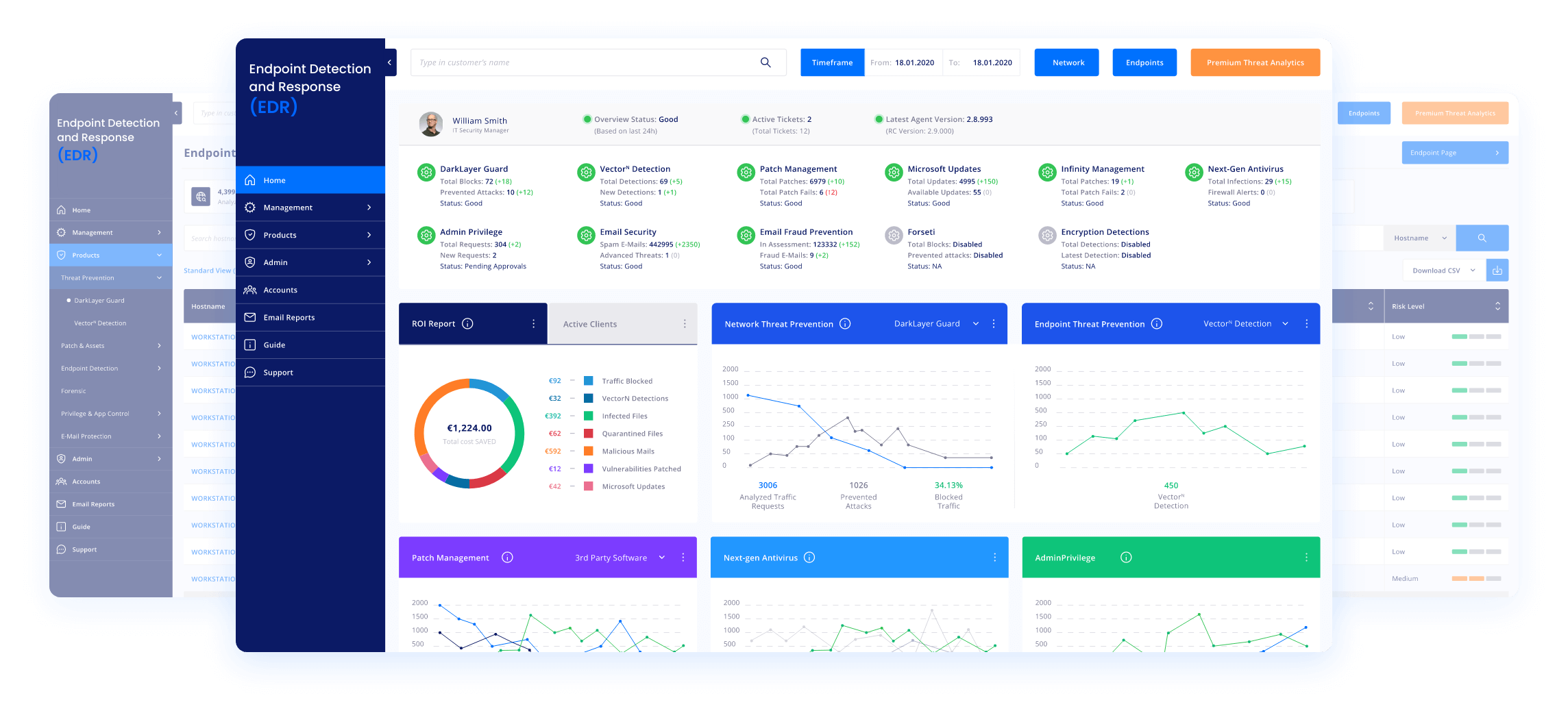
One Unified Dashboard For All Security Modules
One Dashboard to prevent, detect, hunt and respond to any threat, deploy and update any Microsoft, 3rd party and proprietary software, manage assets and ensure compliance
Vulnerability Management
Automate Patch Management, Close Vulnerabilities. Achieve Compliance
Automate your vulnerability management and save valuable time and resources from anywhere in the world and according to any schedule with a patch management solution . Complete visibility and granular control over your entire software inventory.
- Microsoft and Linux Updates made easy
- Automated Patching for 120+ Third-Party applications
- Easy Policy Creation and Deployment
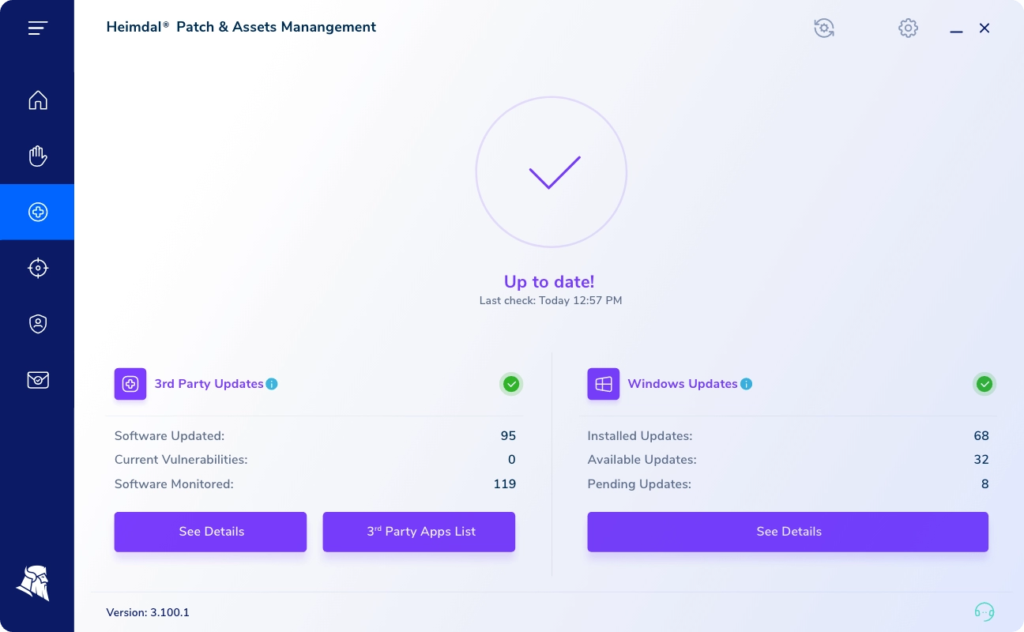
A to Z Patch Management
Patch & Asset Management takes over any updating or patching flow, regardless of licensing options or vendor. Our patch management solution covers Microsoft and Linux OS, 3rd party software, and proprietary through command-line scripting.
Advanced Patch Scheduling
Patch anything, update everything, deploy, and upscale regardless of time-zone, machine availability or versioning. Push for advanced scheduling, force-reboot, on-demand update, patch, or security feature deployment.
Designed for Maximum Efficiency
Capitalize on time and IT resources by allowing your users to safely install, upgrade or downgrade software without over-the-shoulder supervision.
Effortless Software Inventory
Increased visibility over company-owned software assets. One interface for many jobs – updating, patching, downgrading, pushing custom packages, checking software versions, installed volume, and more. All of this under 30 seconds or less
Beyond Compliance
Effortless software inventory means zero compliance issues. Every detail or modification is backlogged, archived, and made ready to be used for extensive inventory reports or compliance audits. The fastest way to obtain the NIST CM-7 controls accreditation
Easy Vulnerability Remediation
Legacy is software familiarity. Get rid of outdated apps and close off the remaining security gaps. Automating the patch management process strengthens overall security, improves software performance, allowing your IT department to focus on more, company-vital, tasks.
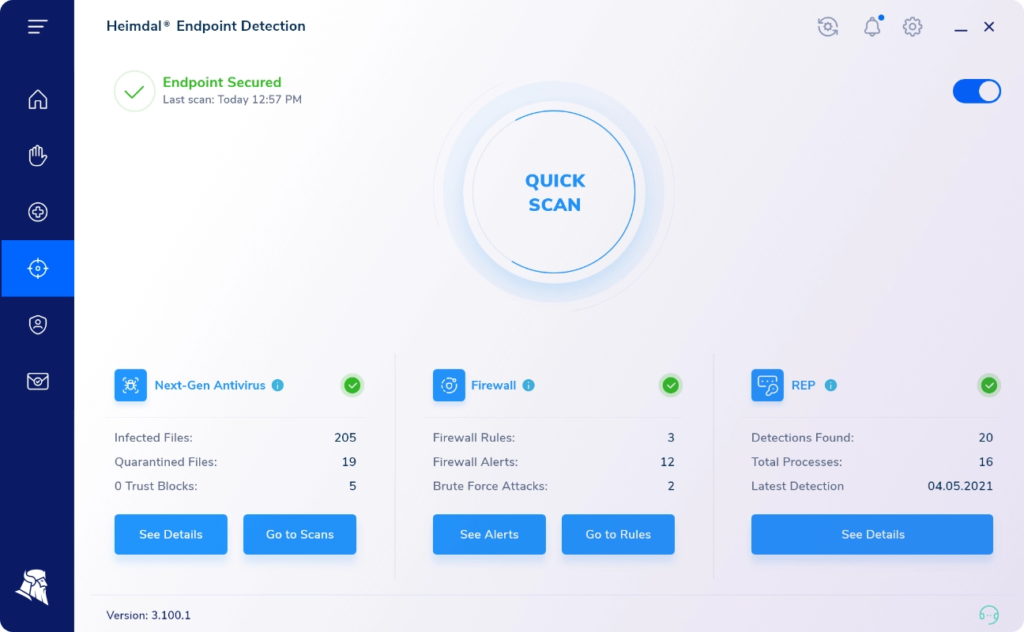
Next Gen Antivirus with MDM
4-Layer Endpoint Antivirus with MDM and Extended Firewall Features
One license and one console – NGAV + XTP with MDM all unified for impeccable detection of sophisticated online threats such as ransomware, hidden backdoors, rootkits, brute-force attacks and undetectable malware.
Multiple layers of detection
Four layers of impeccable detection powered by our unique intelligence to detect and mitigate even the most complex threats.
Enhanced Brute-Force Protection
Unique anti-brute-force safeguards, specially designed to protect you against data leaks.
Remote device control with MDM
Remotely track and manage your Android devices, with easily accessible Locate, Lock and Wipe capabilities from our MDM console
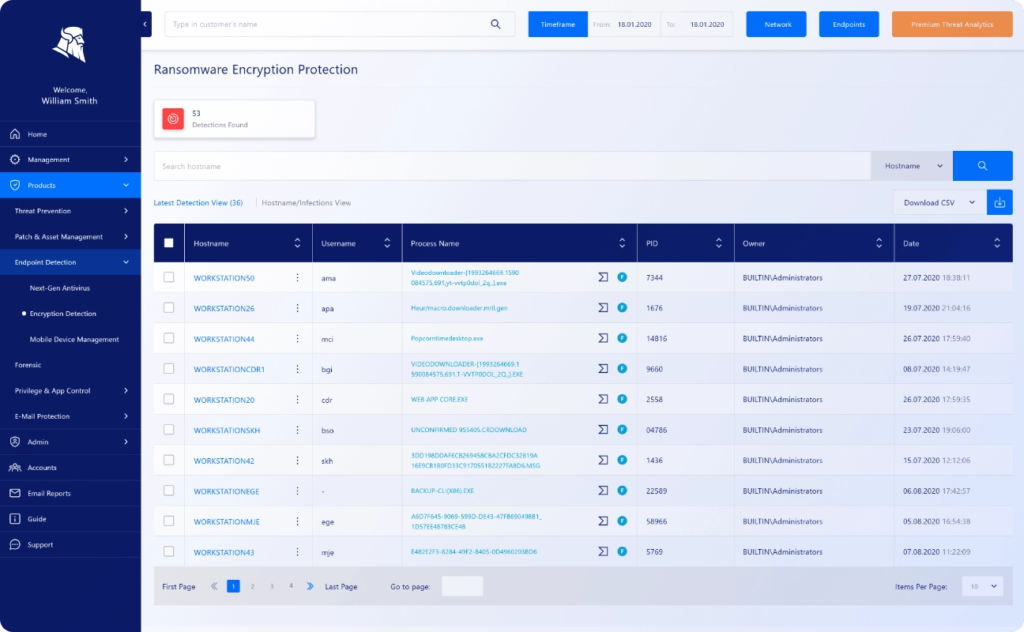
Ransomware Encryption Protection
Protect Your Company From Ransomware Attacks
Revolutionary 100% signature-free solution, that protects your devices against malicious encryption attempts associated with ransomware attacks. Prevent and protect, not just mitigate, both in the cloud & on-prem.
Reducing the detection gap
Our anti-ransomware software has the lowest false-positive rate in the market on account of our Intelligence, which allows us to study malicious behavior in a safe environment
Retracing ransomware attacks
Review incident details such as timestamps, tree diagrams with process callbacks, PowerShell scrips, computed MD5 hash, enumeration of read or write operation performed during encryption attempts, command-line arguments, the signature of malicious process, owner, and many more.
Efficient against unknown threats
No file dependency means our solution can quickly eliminate threat before it has a chance to start encrypting your files. Keep both your endpoints and your Microsoft 365 cloud storage & productivity suite safe against unknown or un-classified ransomware.
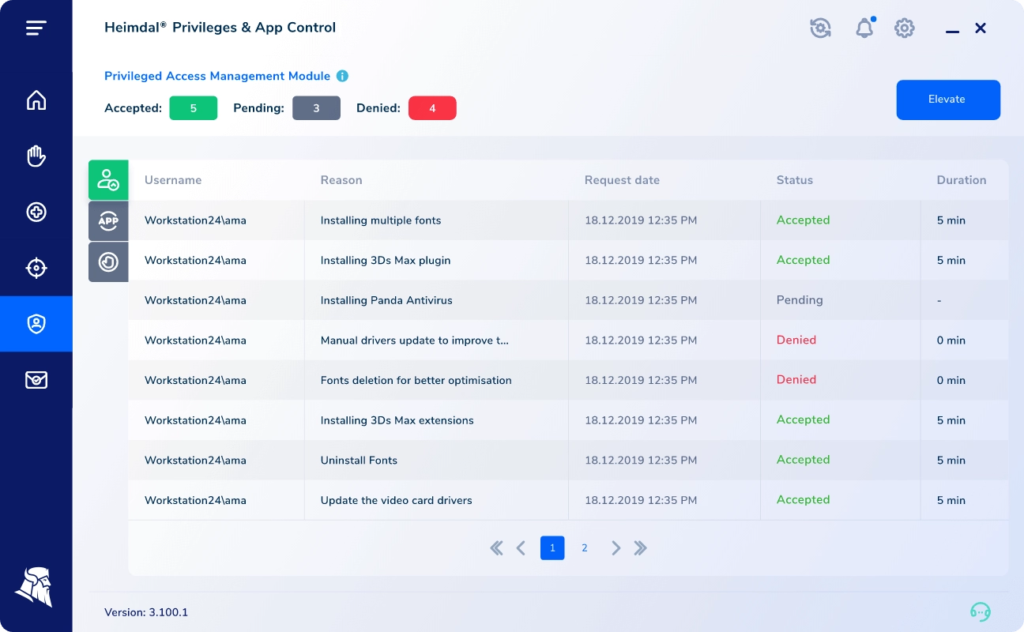
Privileged Access Management
Escalate & de-escalate user rights and manage permissions
Automatic de-escalation of user rights and end the user session whenever a threat is detected on the user’s device.
Lightweight and stunning interface that puts you in complete control over the user’s elevated session. Approve or deny from the dashboard or on the go right from your mobile device. Keep track of sessions, block elevation for system files, live-cancel user admin rights, set escalation period, and instantly shut down system process after session expiration.
Flip on the auto-pilot
Increased mobility, less time spent approving or denying requests. Create approval/denial flows, set individual rights per AD group and escalation period, remove existing local admin rights and more.
Powerful Auditing tools
Quickly fetch graphic-rich reports on hostname details, average escalation duration, users or files escalated, files or processes ran during escalation, and more. Advanced data analytics that will help you investigate incidents and perform regular security checkups.
Identify and remove hidden vulnerabilities
93% of Windows OS and 100% of all browser-specific vulnerabilities can be solved by removing existing admin rights with Privileged Access Management
Application Control
Prevent Unauthorized Application Execution.
Application management solution for whitelisting and blocking of running applications and Prevent users from running malicious software. Customize live sessions, log everything on the go, .
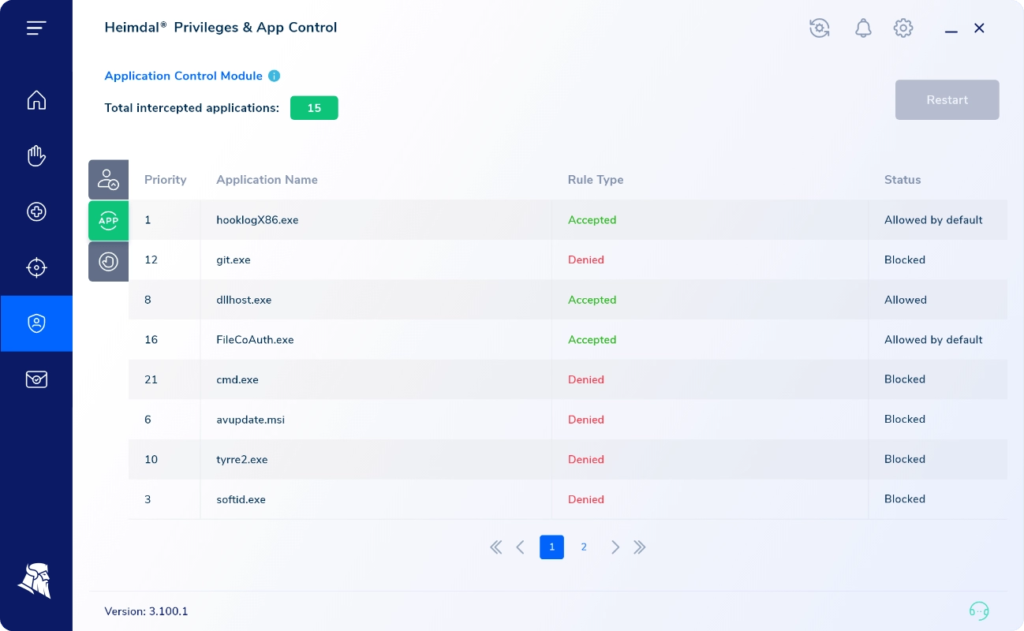
Multiple ways to allow or block applications
App Control allows users to allow or block application execution in more than one way: file path, publisher, certificate, vendor name, software name, MD5, and more. The choice is yours.
Automatic approval or denial flow
Accelerate your application approval or denial flow for system files with default ruling. Create or modify flows for individual users or AD groups.
Dual Modes Operation
Layers upon layers of granularity. Application Control operates in both active and passive mode. Take control of your user’s session or sit back, and let App Control weave its magic.
One Unified Dashboard For All Security Modules
One Dashboard to prevent, detect, hunt and respond to any threat, deploy and update any Microsoft, 3rd party and proprietary software, manage assets and ensure compliance

Download Corporate Brochure
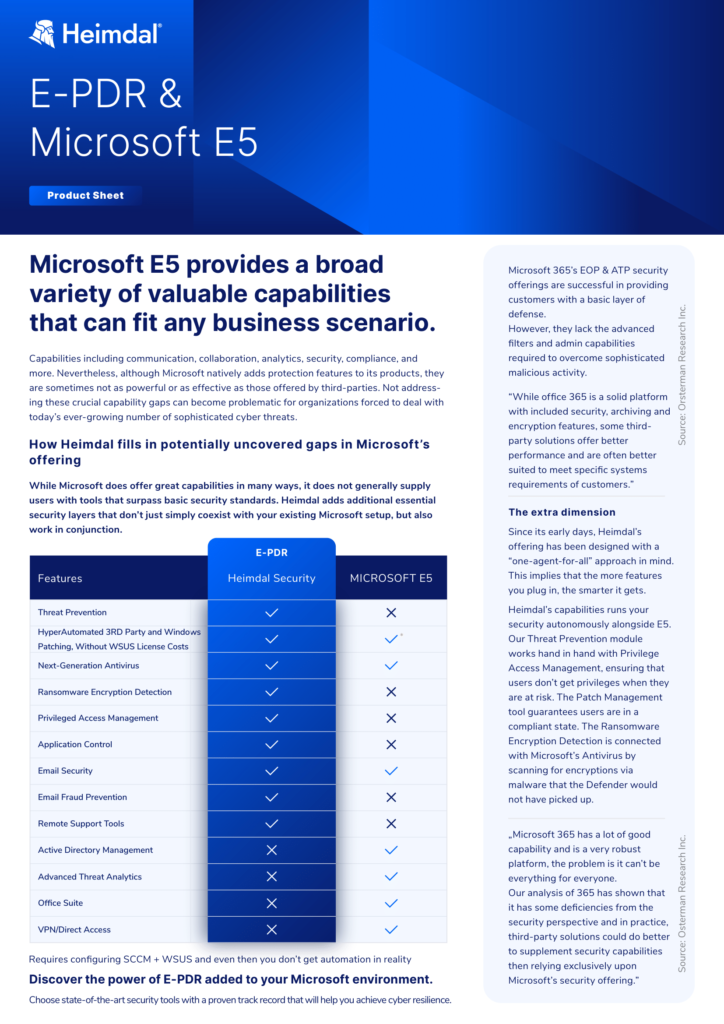
How Heimdal fills in potentially uncovered gaps in Microsoft’s offering
While Microsoft does offer great capabilities in many ways, it does not generally supply users with tools that surpass basic security standards. Heimdal adds additional essential security layers that don’t just simply coexist with your existing Microsoft setup, but also
Product Demo
Heimdal Endpoint Detection & Response (EDR) in Action with Bulwark Technologies
One agent, one platform. Heimdal EDR combines the most advanced threat-hunting technologies in existence: Next-Gen Antivirus, Privileged Access Management, Application Control, Ransomware Encryption Protection, Patch & Asset Management, DNS Traffic Filtering, and threat modeling.
Schedule a FREE Demo
"*" indicates required fields
