iStorage CloudAshur
The future of cloud data security - CloudAshur
iStorage cloudAshur hardware security module is the perfect solution for anyone wanting to securely store, share and manage data in the cloud. cloudAshur can also be used to encrypt data stored on a network drive, on a local PC/MAC and to send encrypted email attachments or data via file sharing software applications.


5-factor authentication process:
Both data at rest and data in transit is encrypted using the cloudAshur module. In order to decrypt data stored in the cloud, on a network drive, on a local PC/MAC, or to decrypt encrypted email attachments or data transferred via file sharing software applications, the user will need to go through an unprecedented 5-factor authentication process:
- Physically have possession of the cloudAshur module
- Know the 7-15 digit PIN (password) which is entered via the cloudAshur onboard keypad
- Know the login credentials for the iStorage client app
- Know where the data is stored (which cloud)
- Know the login credentials for the cloud account
iStorage cloudAshur allows you to
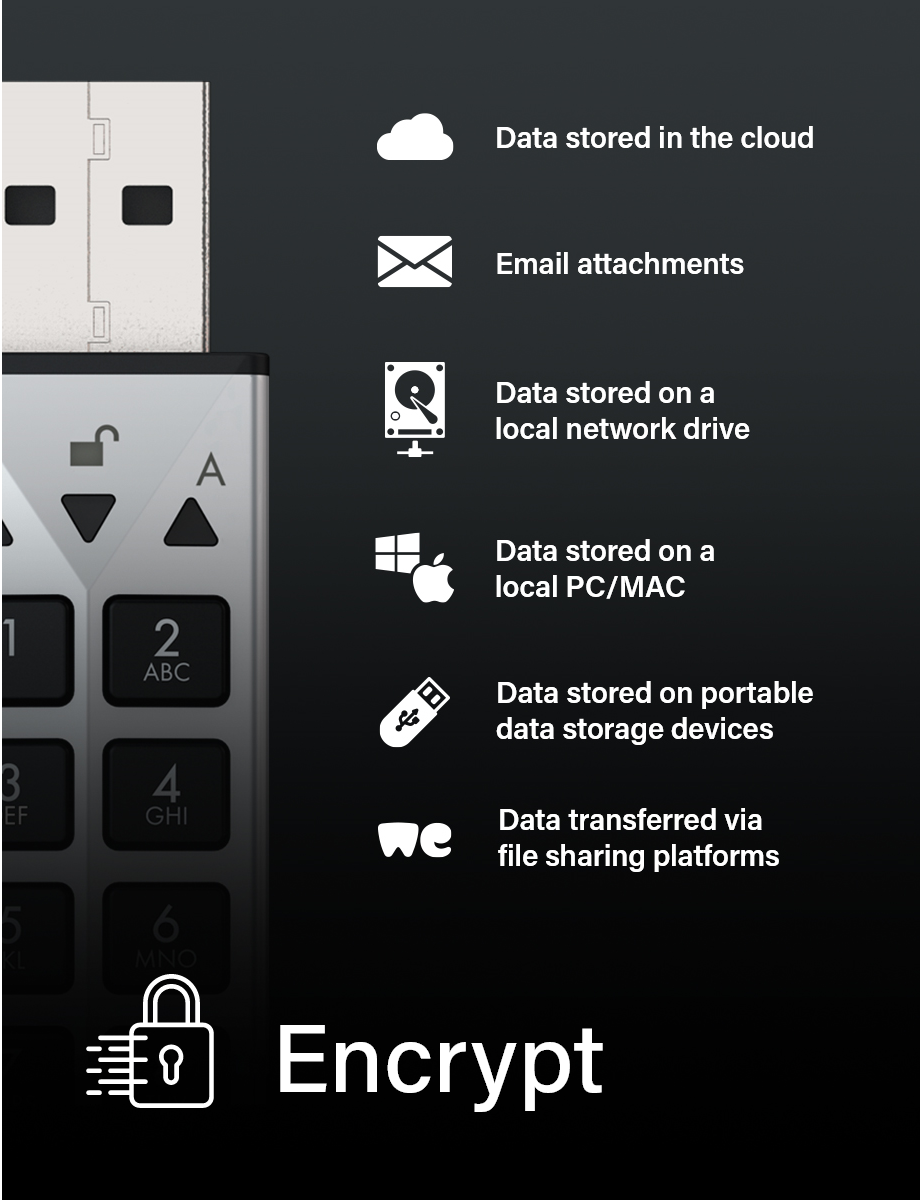
ENCRYPT to ensure the ultimate security of data stored in the cloud or on a local network drive, local PC/MAC or any data storage device

SHARE encrypted data securely with authorised users in the cloud, on a local network drive, via email and with file transfer services in real-time

MANAGE and monitor cloudAshur devices centrally
Benefits of using the cloudAshur

Regulatory compliance
Users can rest assured that hackers won’t be able to decrypt data stored in the cloud
5 Factor Authentication
This makes it virtually impossible to hack data that is stored in the cloud.
You are in Control
The user holds the encrypted encryption key to their data in the securest way possible. There is no need to be concerned about data in the cloud being viewed, stolen or shared
Human error no longer an issue
With the cloudAshur Remote Management Console manage all cloudAshur modules deployed within an organisation. remotely disable or reset a cloudAshur module if lost or stolen.
Protection against cloud provider personnel, who can access user data
With the cloudAshur, data is encrypted at client side and the user controls the encryption key.
iStorage products range you might be interested in
Request a FREE Evaluation from iStorage Product Range



